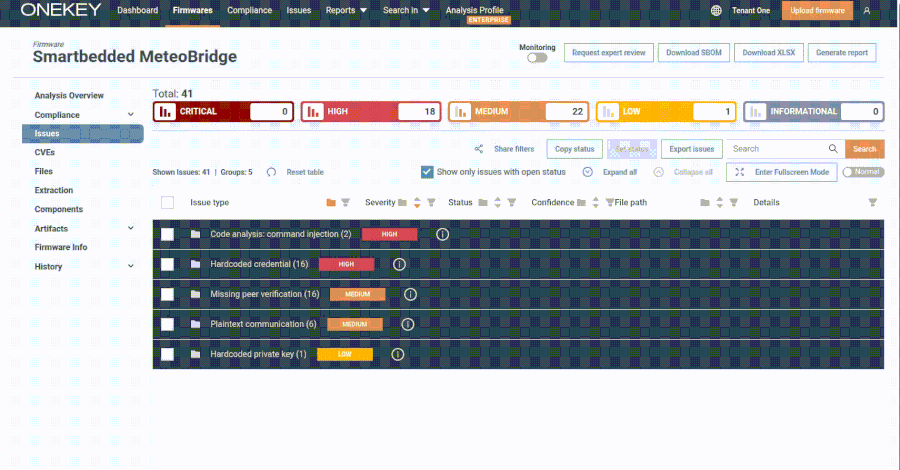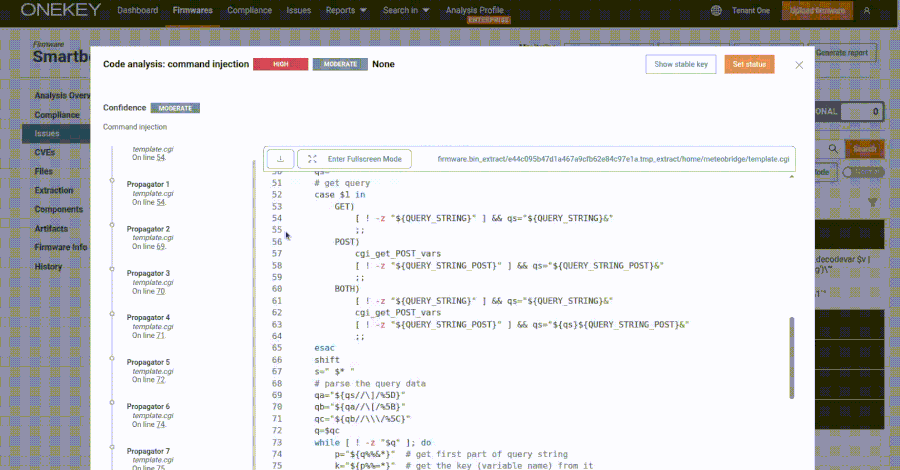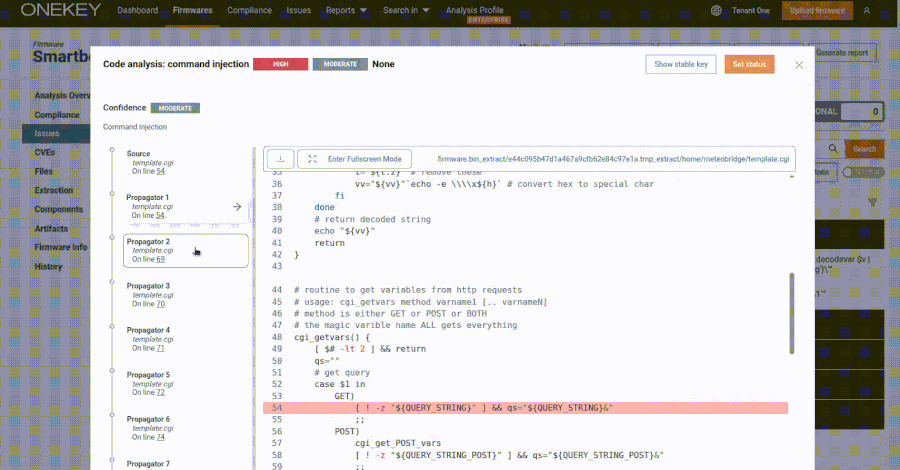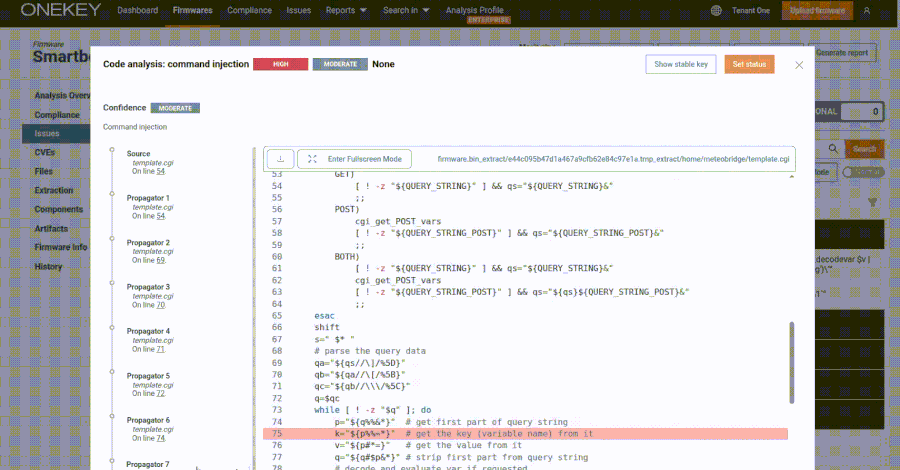
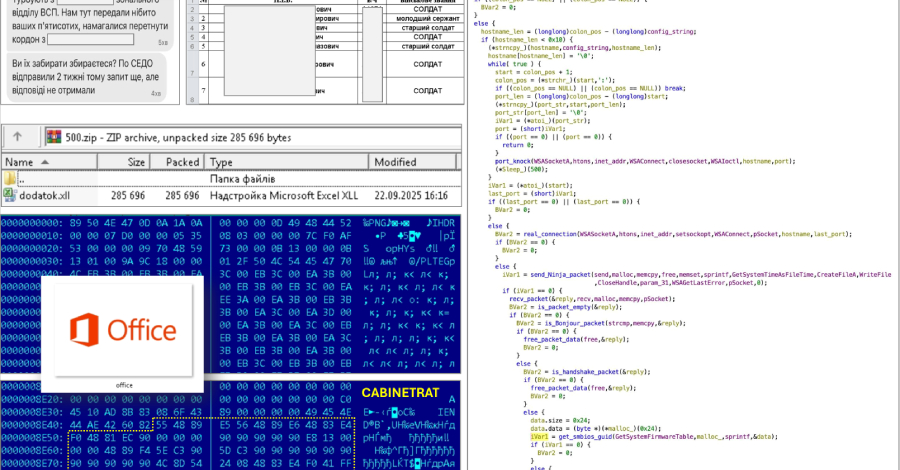
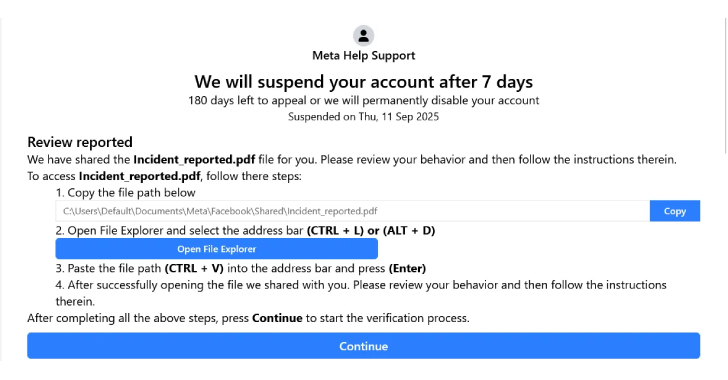
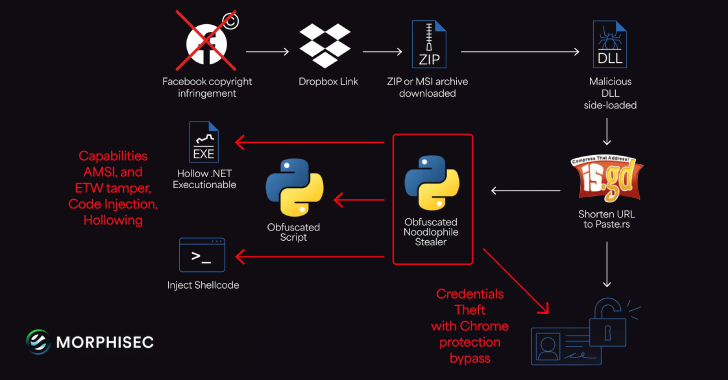
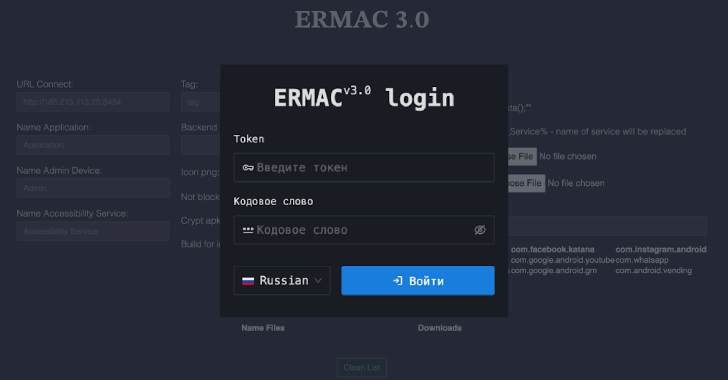
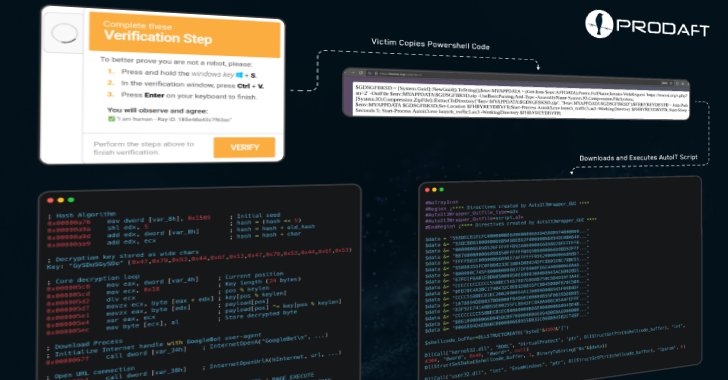
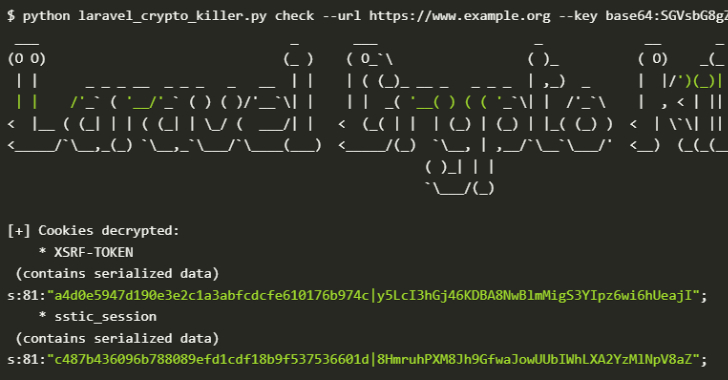
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Hackers Target ICTBroadcast Servers via Cookie Exploit to Gain Remote Shell Access
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
New SAP NetWeaver Bug Lets Attackers Take Over Servers Without Login
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
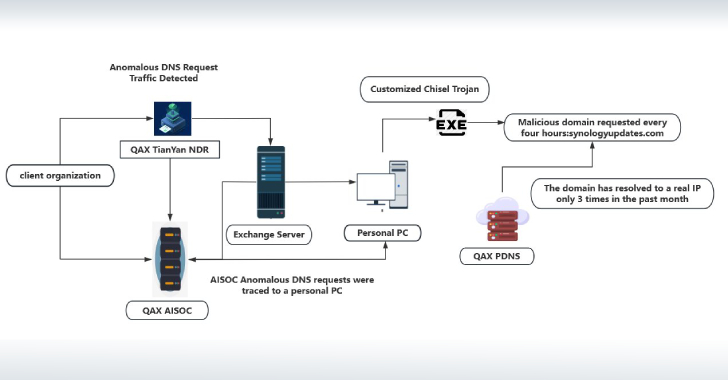
Chinese Hackers Exploit ArcGIS Server as Backdoor for Over a Year
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Moving Beyond Awareness: How Threat Hunting Builds Readiness
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
What AI Reveals About Web Applications— and Why It Matters
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
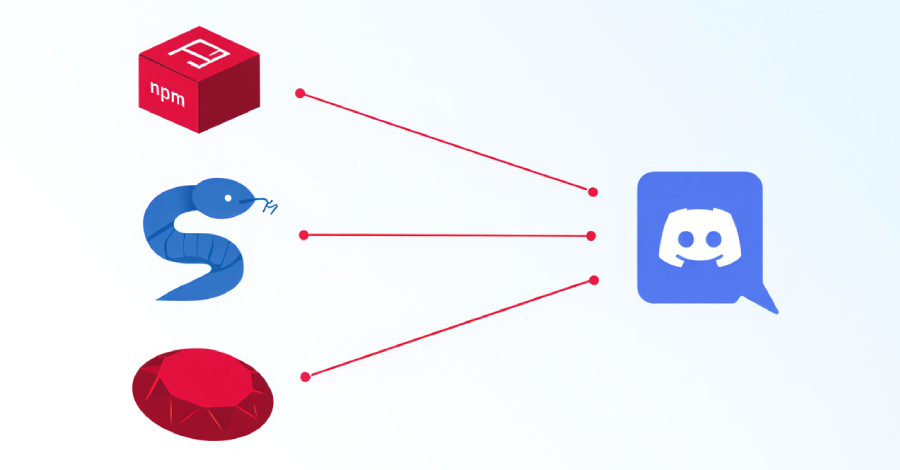
npm, PyPI, and RubyGems Packages Found Sending Developer Data to Discord Channels
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Researchers Expose TA585’s MonsterV2 Malware Capabilities and Attack Chain
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
⚡ Weekly Recap: WhatsApp Worm, Critical CVEs, Oracle 0-Day, Ransomware Cartel & More
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Why Unmonitored JavaScript Is Your Biggest Holiday Security Risk
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
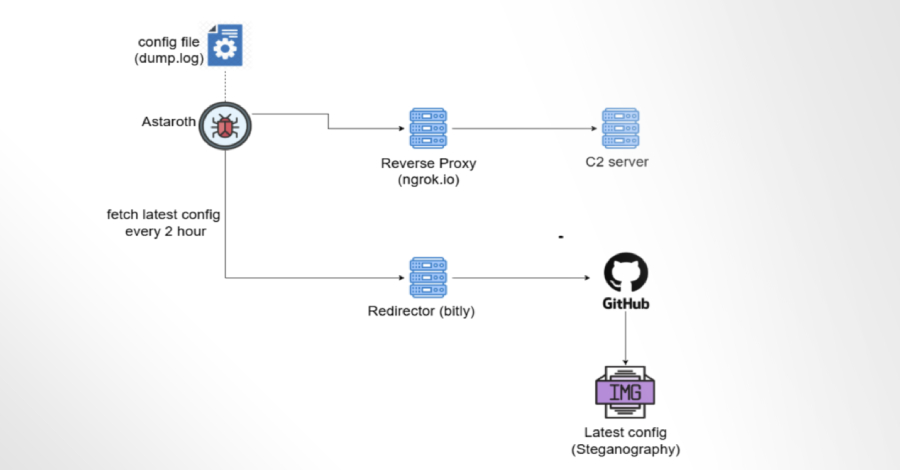
Astaroth Banking Trojan Abuses GitHub to Remain Operational After Takedowns
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
New Oracle E-Business Suite Bug Could Let Hackers Access Data Without Login
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Stealit Malware Abuses Node.js Single Executable Feature via Game and VPN Installers
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Microsoft Warns of ‘Payroll Pirates’ Hijacking HR SaaS Accounts to Steal Employee Salaries
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
From Detection to Patch: Fortra Reveals Full Timeline of CVE-2025-10035 Exploitation
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
The AI SOC Stack of 2026: What Sets Top-Tier Platforms Apart?
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
175 Malicious npm Packages with 26,000 Downloads Used in Credential Phishing Campaign
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
From LFI to RCE: Active Exploitation Detected in Gladinet and TrioFox Vulnerability
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
ThreatsDay Bulletin: MS Teams Hack, MFA Hijacking, $2B Crypto Heist, Apple Siri Probe & More
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
SaaS Breaches Start with Tokens – What Security Teams Must Watch
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Critical Exploit Lets Hackers Bypass Authentication in WordPress Service Finder Theme
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Chinese Hackers Weaponize Open-Source Nezha Tool in New Attack Wave
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
No Time to Waste: Embedding AI to Cut Noise and Reduce Risk
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
OpenAI Disrupts Russian, North Korean, and Chinese Hackers Misusing ChatGPT for Cyberattacks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Google's New AI Doesn't Just Find Vulnerabilities — It Rewrites Code to Patch Them
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
XWorm 6.0 Returns with 35+ Plugins and Enhanced Data Theft Capabilities
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
13-Year-Old Redis Flaw Exposed: CVSS 10.0 Vulnerability Lets Attackers Run Code Remotely
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
5 Critical Questions For Adopting an AI Security Solution
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Oracle Rushes Patch for CVE-2025-61882 After Cl0p Exploited It in Data Theft Attacks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Scanning Activity on Palo Alto Networks Portals Jump 500% in One Day
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Detour Dog Caught Running DNS-Powered Malware Factory for Strela Stealer
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Rhadamanthys Stealer Evolves: Adds Device Fingerprinting, PNG Steganography Payloads
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Researchers Warn of Self-Spreading WhatsApp Malware Named SORVEPOTEL
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
New "Cavalry Werewolf" Attack Hits Russian Agencies with FoalShell and StallionRAT
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Automating Pentest Delivery: 7 Key Workflows for Maximum Impact
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
ThreatsDay Bulletin: CarPlay Exploit, BYOVD Tactics, SQL C2 Attacks, iCloud Backdoor Demand & More
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Google Mandiant Probes New Oracle Extortion Wave Possibly Linked to Cl0p Ransomware
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
How to Close Threat Detection Gaps: Your SOC's Action Plan
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
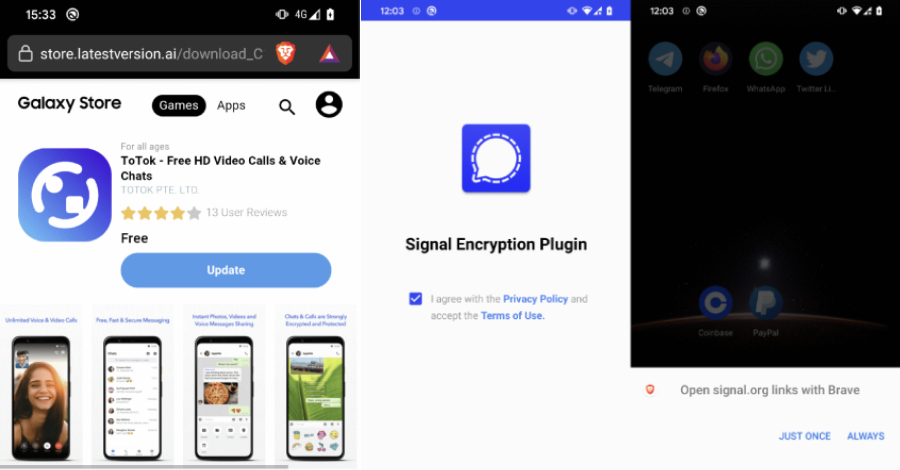
Warning: Beware of Android Spyware Disguised as Signal Encryption Plugin and ToTok Pro
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
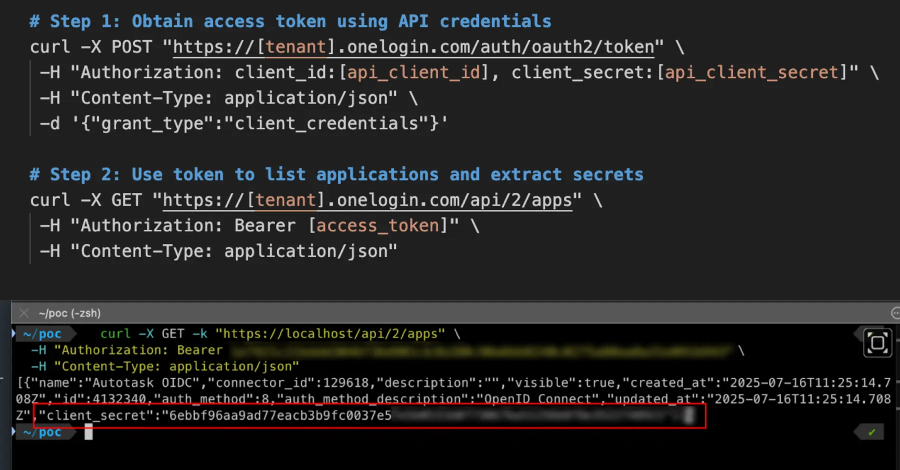
OneLogin Bug Let Attackers Use API Keys to Steal OIDC Secrets and Impersonate Apps
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Hackers Exploit Milesight Routers to Send Phishing SMS to European Users
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
2025 Cybersecurity Reality Check: Breaches Hidden, Attack Surfaces Growing, and AI Misperceptions Rising
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
New Android Banking Trojan “Klopatra” Uses Hidden VNC to Control Infected Smartphones
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
New $50 Battering RAM Attack Breaks Intel and AMD Cloud Security Protections
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
$50 Battering RAM Attack Breaks Intel and AMD Cloud Security Protections
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Phantom Taurus: New China-Linked Hacker Group Hits Governments With Stealth Malware
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Researchers Disclose Google Gemini AI Flaws Allowing Prompt Injection and Cloud Exploits
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Microsoft Expands Sentinel Into Agentic Security Platform With Unified Data Lake
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Stop Alert Chaos: Context Is the Key to Effective Incident Response
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Urgent: China-Linked Hackers Exploit New VMware Zero-Day Since October 2024
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
New Android Trojan “Datzbro” Tricking Elderly with AI-Generated Facebook Travel Events
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Evolving Enterprise Defense to Secure the Modern AI Supply Chain
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
U.K. Police Just Seized £5.5 Billion in Bitcoin — The World’s Largest Crypto Bust
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
CISA Sounds Alarm on Critical Sudo Flaw Actively Exploited in Linux and Unix Systems
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
EvilAI Malware Masquerades as AI Tools to Infiltrate Global Organizations
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
⚡ Weekly Recap: Cisco 0-Day, Record DDoS, LockBit 5.0, BMC Bugs, ShadowV2 Botnet & More
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
The State of AI in the SOC 2025 – Insights from Recent Study
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Microsoft Flags AI-Driven Phishing: LLM-Crafted SVG Files Outsmart Email Security
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
First Malicious MCP Server Found Stealing Emails in Rogue Postmark-MCP Package
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
China-Linked PlugX and Bookworm Malware Attacks Target Asian Telecom and ASEAN Networks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Researchers Expose Phishing Threats Distributing CountLoader and PureRAT
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
New COLDRIVER Malware Campaign Joins BO Team and Bearlyfy in Russia-Focused Cyberattacks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Crash Tests for Security: Why BAS Is Proof of Defense, Not Assumptions
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
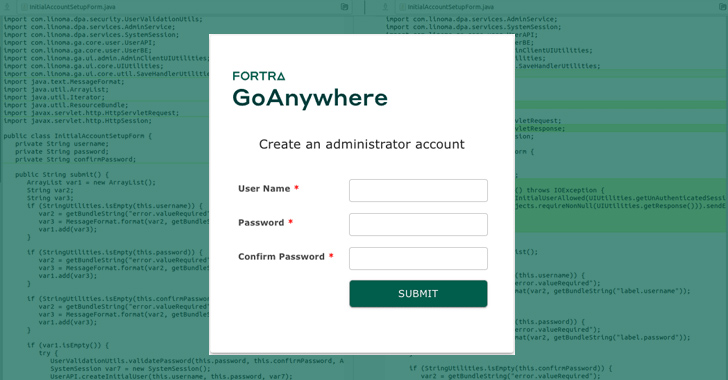
Fortra GoAnywhere CVSS 10 Flaw Exploited as 0-Day a Week Before Public Disclosure
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
New macOS XCSSET Variant Targets Firefox with Clipper and Persistence Module
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Cisco ASA Firewall Zero-Day Exploits Deploy RayInitiator and LINE VIPER Malware
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Urgent: Cisco ASA Zero-Day Duo Under Attack; CISA Triggers Emergency Mitigation Directive
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Threatsday Bulletin: Rootkit Patch, Federal Breach, OnePlus SMS Leak, TikTok Scandal & More
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Vane Viper Generates 1 Trillion DNS Queries to Power Global Malware and Ad Fraud Network
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Salesforce Patches Critical ForcedLeak Bug Exposing CRM Data via AI Prompt Injection
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
North Korean Hackers Use New AkdoorTea Backdoor to Target Global Crypto Developers
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
CTEM's Core: Prioritization and Validation
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Tech Overtakes Gaming as Top DDoS Attack Target, New Gcore Radar Report Finds
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Malicious Rust Crates Steal Solana and Ethereum Keys — 8,424 Downloads Confirmed
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Cisco Warns of Actively Exploited SNMP Vulnerability Allowing RCE or DoS in IOS Software
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Chinese Hackers RedNovember Target Global Governments Using Pantegana and Cobalt Strike
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
UNC5221 Uses BRICKSTORM Backdoor to Infiltrate U.S. Legal and Technology Sectors
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Two Critical Flaws Uncovered in Wondershare RepairIt Exposing User Data and AI Models
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
How One Bad Password Ended a 158-Year-Old Business
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
New YiBackdoor Malware Shares Major Code Overlaps with IcedID and Latrodectus
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
iframe Security Exposed: The Blind Spot Fueling Payment Skimmer Attacks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Hackers Exploit Pandoc CVE-2025-51591 to Target AWS IMDS and Steal EC2 IAM Credentials
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
State-Sponsored Hackers Exploiting Libraesva Email Security Gateway Vulnerability
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Two New Supermicro BMC Bugs Allow Malicious Firmware to Evade Root of Trust Security
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Eurojust Arrests 5 in €100M Cryptocurrency Investment Fraud Spanning 23 Countries
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
U.S. Secret Service Seizes 300 SIM Servers, 100K Cards Threatening U.S. Officials Near UN
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
SolarWinds Releases Hotfix for Critical CVE-2025-26399 Remote Code Execution Flaw
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Lean Teams, Higher Stakes: Why CISOs Must Rethink Incident Remediation
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
ShadowV2 Botnet Exploits Misconfigured AWS Docker Containers for DDoS-for-Hire Service
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
GitHub Mandates 2FA and Short-Lived Tokens to Strengthen npm Supply Chain Security
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
BadIIS Malware Spreads via SEO Poisoning — Redirects Traffic, Plants Web Shells
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
ComicForm and SectorJ149 Hackers Deploy Formbook Malware in Eurasian Cyberattacks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
⚡ Weekly Recap: Chrome 0-Day, AI Hacking Tools, DDR5 Bit-Flips, npm Worm & More
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
How to Gain Control of AI Agents and Non-Human Identities
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Microsoft Patches Critical Entra ID Flaw Enabling Global Admin Impersonation Across Tenants
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
DPRK Hackers Use ClickFix to Deliver BeaverTail Malware in Crypto Job Scams
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
LastPass Warns of Fake Repositories Infecting macOS with Atomic Infostealer
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Researchers Uncover GPT-4-Powered MalTerminal Malware Creating Ransomware, Reverse Shell
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
ShadowLeak Zero-Click Flaw Leaks Gmail Data via OpenAI ChatGPT Deep Research Agent
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
SonicWall Urges Password Resets After Cloud Backup Breach Affecting Under 5% of Customers
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
CountLoader Broadens Russian Ransomware Operations With Multi-Version Malware Loader
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
SilentSync RAT Delivered via Two Malicious PyPI Packages Targeting Python Developers
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
How CISOs Can Drive Effective AI Governance
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Google Patches Chrome Zero-Day CVE-2025-10585 as Active V8 Exploit Threatens Millions
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
TA558 Uses AI-Generated Scripts to Deploy Venom RAT in Brazil Hotel Attacks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Chinese TA415 Uses VS Code Remote Tunnels to Spy on U.S. Economic Policy Experts
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
From Quantum Hacks to AI Defenses – Expert Guide to Building Unbreakable Cyber Resilience
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Rethinking AI Data Security: A Buyer's Guide
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Scattered Spider Resurfaces With Financial Sector Attacks Despite Retirement Claims
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
DOJ Resentences BreachForums Founder to 3 Years for Cybercrime and Possession of CSAM
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
RaccoonO365 Phishing Network Dismantled as Microsoft, Cloudflare Take Down 338 Domains
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Chaos Mesh Critical GraphQL Flaws Enable RCE and Full Kubernetes Cluster Takeover
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
SlopAds Fraud Ring Exploits 224 Android Apps to Drive 2.3 Billion Daily Ad Bids
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
New FileFix Variant Delivers StealC Malware Through Multilingual Phishing Site
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Apple Backports Fix for CVE-2025-43300 Exploited in Sophisticated Spyware Attack
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Securing the Agentic Era: Introducing Astrix's AI Agent Control Plane
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
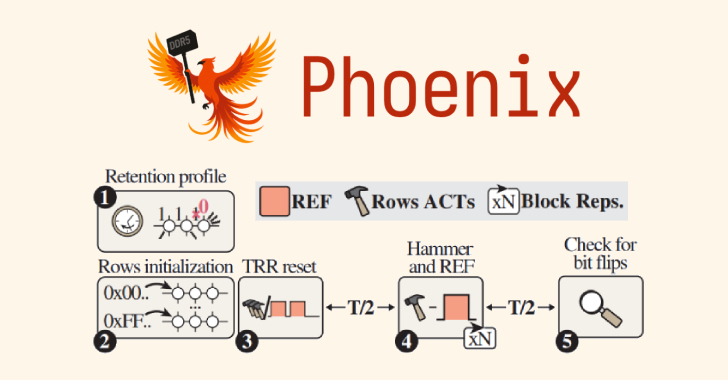
Phoenix RowHammer Attack Bypasses Advanced DDR5 Memory Protections in 109 Seconds
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Self-Replicating Worm Hits 180+ npm Packages to Steal Credentials in Latest Supply Chain Attack
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Mustang Panda Deploys SnakeDisk USB Worm to Deliver Yokai Backdoor on Thailand IPs
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
6 Browser-Based Attacks Security Teams Need to Prepare For Right Now
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
⚡ Weekly Recap: Bootkit Malware, AI-Powered Attacks, Supply Chain Breaches, Zero-Days & More
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
AI-Powered Villager Pen Testing Tool Hits 11,000 PyPI Downloads Amid Abuse Concerns
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
HiddenGh0st, Winos and kkRAT Exploit SEO, GitHub Pages in Chinese Malware Attacks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
FBI Warns of UNC6040 and UNC6395 Targeting Salesforce Platforms in Data Theft Attacks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Samsung Fixes Critical Zero-Day CVE-2025-21043 Exploited in Android Attacks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Apple Warns French Users of Fourth Spyware Campaign in 2025, CERT-FR Confirms
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
New HybridPetya Ransomware Bypasses UEFI Secure Boot With CVE-2024-7344 Exploit
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Critical CVE-2025-5086 in DELMIA Apriso Actively Exploited, CISA Issues Warning
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Cloud-Native Security in 2025: Why Runtime Visibility Must Take Center Stage
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Cursor AI Code Editor Flaw Enables Silent Code Execution via Malicious Repositories
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Google Pixel 10 Adds C2PA Support to Verify AI-Generated Media Authenticity
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Senator Wyden Urges FTC to Probe Microsoft for Ransomware-Linked Cybersecurity Negligence
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Cracking the Boardroom Code: Helping CISOs Speak the Language of Business
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
SonicWall SSL VPN Flaw and Misconfigurations Actively Exploited by Akira Ransomware Hackers
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Fake Madgicx Plus and SocialMetrics Extensions Are Hijacking Meta Business Accounts
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
AsyncRAT Exploits ConnectWise ScreenConnect to Steal Credentials and Crypto
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Chinese APT Deploys EggStreme Fileless Malware to Breach Philippine Military Systems
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
CHILLYHELL macOS Backdoor and ZynorRAT RAT Threaten macOS, Windows, and Linux Systems
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Microsoft Fixes 80 Flaws — Including SMB PrivEsc and Azure CVSS 10.0 Bugs
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Apple iPhone Air and iPhone 17 Feature A19 Chips With Spyware-Resistant Memory Safety
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
The Time-Saving Guide for Service Providers: Automating vCISO and Compliance Services
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Watch Out for Salty2FA: New Phishing Kit Targeting US and EU Enterprises
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
China-Linked APT41 Hackers Target U.S. Trade Officials Amid 2025 Negotiations
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Adobe Commerce Flaw CVE-2025-54236 Lets Hackers Take Over Customer Accounts
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
SAP Patches Critical NetWeaver (CVSS Up to 10.0) and High-Severity S/4HANA Flaws
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Axios Abuse and Salty 2FA Kits Fuel Advanced Microsoft 365 Phishing Attacks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
RatOn Android Malware Detected With NFC Relay and ATS Banking Fraud Capabilities
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
[Webinar] Shadow AI Agents Multiply Fast — Learn How to Detect and Control Them
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
From MostereRAT to ClickFix: New Malware Campaigns Highlight Rising AI and Phishing Risks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
How Leading CISOs are Getting Budget Approval
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
TOR-Based Cryptojacking Attack Expands Through Misconfigured Docker APIs
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
20 Popular npm Packages With 2 Billion Weekly Downloads Compromised in Supply Chain Attack
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
45 Previously Unreported Domains Expose Longstanding Salt Typhoon Cyber Espionage
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
GitHub Account Compromise Led to Salesloft Drift Breach Affecting 22 Companies
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
GPUGate Malware Uses Google Ads and Fake GitHub Commits to Target IT Firms
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
⚡ Weekly Recap: Drift Breach Chaos, Zero-Days Active, Patch Warnings, Smarter Threats & More
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
You Didn’t Get Phished — You Onboarded the Attacker
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Noisy Bear Campaign Targeting Kazakhstan Energy Sector Outed as a Planned Phishing Test
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Malicious npm Packages Impersonate Flashbots, Steal Ethereum Wallet Keys
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
CISA Orders Immediate Patch of Critical Sitecore Vulnerability Under Active Exploitation
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
TAG-150 Develops CastleRAT in Python and C, Expanding CastleLoader Malware Operations
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
SAP S/4HANA Critical Vulnerability CVE-2025-42957 Exploited in the Wild
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
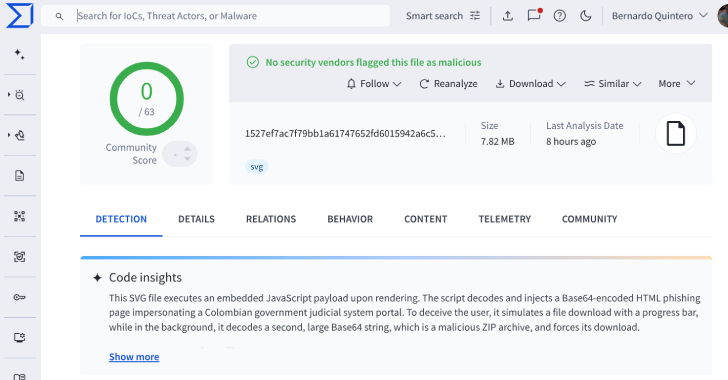
VirusTotal Finds 44 Undetected SVG Files Used to Deploy Base64-Encoded Phishing Pages
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Russian APT28 Deploys “NotDoor” Outlook Backdoor Against Companies in NATO Countries
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
GhostRedirector Hacks 65 Windows Servers Using Rungan Backdoor and Gamshen IIS Module
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Cybercriminals Exploit X’s Grok AI to Bypass Ad Protections and Spread Malware to Millions
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Google Fined $379 Million by French Regulator for Cookie Consent Violations
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
CISA Flags TP-Link Router Flaws CVE-2023-50224 and CVE-2025-9377 as Actively Exploited
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Malicious npm Packages Exploit Ethereum Smart Contracts to Target Crypto Developers
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Threat Actors Weaponize HexStrike AI to Exploit Citrix Flaws Within a Week of Disclosure
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Detecting Data Leaks Before Disaster
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Android Security Alert: Google Patches 120 Flaws, Including Two Zero-Days Under Attack
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Iranian Hackers Exploit 100+ Embassy Email Accounts in Global Phishing Targeting Diplomats
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Cloudflare Blocks Record-Breaking 11.5 Tbps DDoS Attack
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
CISA Adds TP-Link and WhatsApp Flaws to KEV Catalog Amid Active Exploitation
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Salesloft Takes Drift Offline After OAuth Token Theft Hits Hundreds of Organizations
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Lazarus Group Expands Malware Arsenal With PondRAT, ThemeForestRAT, and RemotePE
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Researchers Warn of MystRodX Backdoor Using DNS and ICMP Triggers for Stealthy Control
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Shadow AI Discovery: A Critical Part of Enterprise AI Governance
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Ukrainian Network FDN3 Launches Massive Brute-Force Attacks on SSL VPN and RDP Devices
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Silver Fox Exploits Microsoft-Signed WatchDog Driver to Deploy ValleyRAT Malware
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Malicious npm Package nodejs-smtp Mimics Nodemailer, Targets Atomic and Exodus Wallets
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Android Droppers Now Deliver SMS Stealers and Spyware, Not Just Banking Trojans
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
⚡ Weekly Recap: WhatsApp 0-Day, Docker Bug, Salesforce Breach, Fake CAPTCHAs, Spyware App & More
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
When Browsers Become the Attack Surface: Rethinking Security for Scattered Spider
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
ScarCruft Uses RokRAT Malware in Operation HanKook Phantom Targeting South Korean Academics
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Attackers Abuse Velociraptor Forensic Tool to Deploy Visual Studio Code for C2 Tunneling
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
WhatsApp Patches Zero-Click Exploit Targeting iOS and macOS Devices
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
WhatsApp Issues Emergency Update for Zero-Click Exploit Targeting iOS and macOS Devices
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Researchers Warn of Sitecore Exploit Chain Linking Cache Poisoning and Remote Code Execution
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Amazon Disrupts APT29 Watering Hole Campaign Abusing Microsoft Device Code Authentication
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Abandoned Sogou Zhuyin Update Server Hijacked, Weaponized in Taiwan Espionage Campaign
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Can Your Security Stack See ChatGPT? Why Network Visibility Matters
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Click Studios Patches Passwordstate Authentication Bypass Vulnerability in Emergency Access Page
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
FreePBX Servers Targeted by Zero-Day Flaw, Emergency Patch Now Available
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
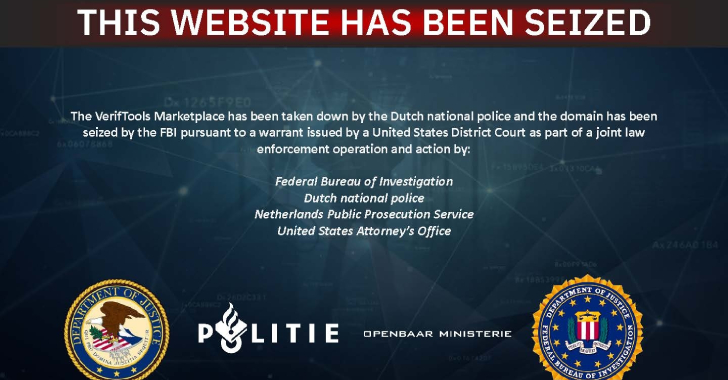
Feds Seize $6.4M VerifTools Fake-ID Marketplace, but Operators Relaunch on New Domain
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Google Warns Salesloft Drift Breach Impacts All Drift Integrations Beyond Salesforce
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Researchers Find VS Code Flaw Allowing Attackers to Republish Deleted Extensions Under Same Names
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Salt Typhoon Exploits Flaws in Edge Network Devices to Breach 600 Organizations Worldwide
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Hidden Vulnerabilities of Project Management Tools & How FluentPro Backup Secures Them
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Malicious Nx Packages in ‘s1ngularity’ Attack Leaked 2,349 GitHub, Cloud, and AI Credentials
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
U.S. Treasury Sanctions DPRK IT-Worker Scheme, Exposing $600K Crypto Transfers and $1M+ Profits
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
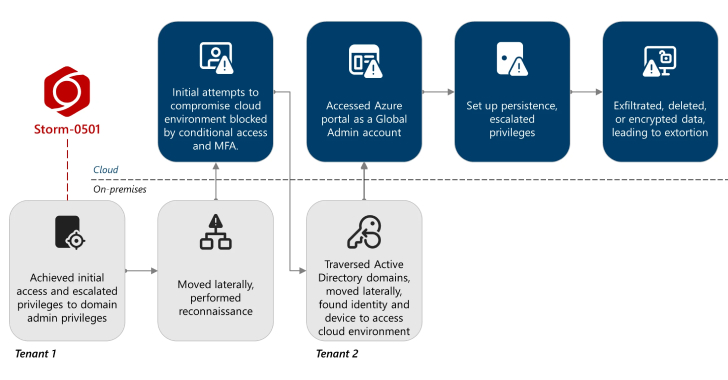
Storm-0501 Exploits Entra ID to Exfiltrate and Delete Azure Data in Hybrid Cloud Attacks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Anthropic Disrupts AI-Powered Cyberattacks Automating Theft and Extortion Across Critical Sectors
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
The 5 Golden Rules of Safe AI Adoption
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Blind Eagle’s Five Clusters Target Colombia Using RATs, Phishing Lures, and Dynamic DNS Infra
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Citrix Patches Three NetScaler Flaws, Confirms Active Exploitation of CVE-2025-7775
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
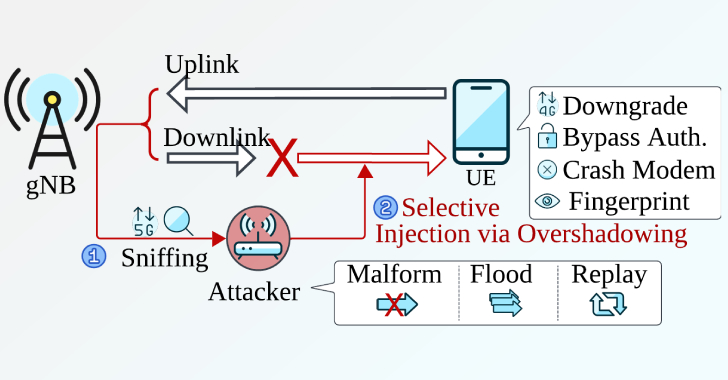
New Sni5Gect Attack Crashes Phones and Downgrades 5G to 4G without Rogue Base Station
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
MixShell Malware Delivered via Contact Forms Targets U.S. Supply Chain Manufacturers
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
ShadowCaptcha Exploits WordPress Sites to Spread Ransomware, Info Stealers, and Crypto Miners
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
UNC6384 Deploys PlugX via Captive Portal Hijacks and Valid Certificates Targeting Diplomats
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Docker Fixes CVE-2025-9074, Critical Container Escape Vulnerability With CVSS Score 9.3
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
⚡ Weekly Recap: Password Manager Flaws, Apple 0-Day, Hidden AI Prompts, In-the-Wild Exploits & More
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Why SIEM Rules Fail and How to Fix Them: Insights from 160 Million Attack Simulations
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Transparent Tribe Targets Indian Govt With Weaponized Desktop Shortcuts via Phishing
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Malicious Go Module Poses as SSH Brute-Force Tool, Steals Credentials via Telegram Bot
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
GeoServer Exploits, PolarEdge, and Gayfemboy Push Cybercrime Beyond Traditional Botnets
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Chinese Hackers Murky, Genesis, and Glacial Panda Escalate Cloud and Telecom Espionage
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Automation Is Redefining Pentest Delivery
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
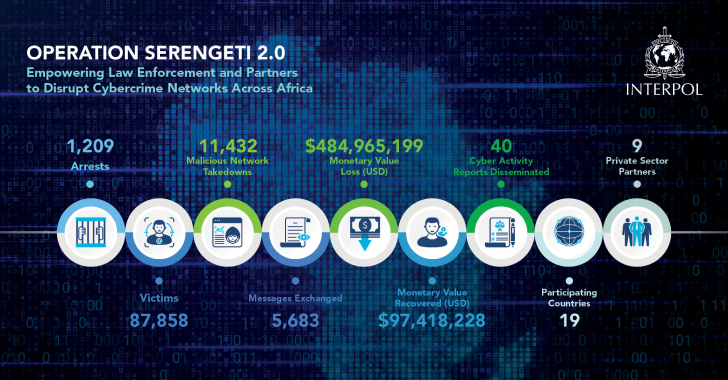
INTERPOL Arrests 1,209 Cybercriminals Across 18 African Nations in Global Crackdown
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Ex-Developer Jailed Four Years for Sabotaging Ohio Employer with Kill-Switch Malware
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
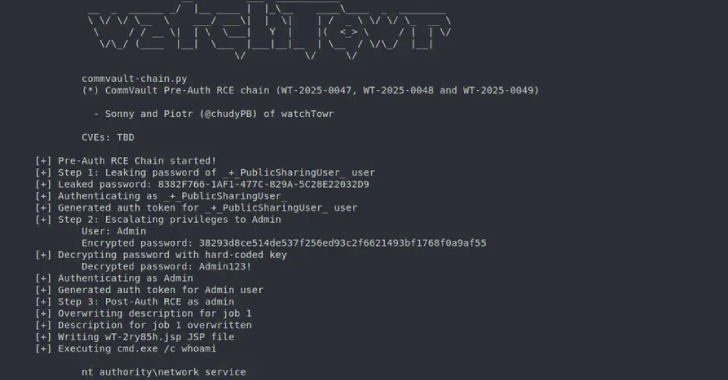
Pre-Auth Exploit Chains Found in Commvault Could Enable Remote Code Execution Attacks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Cybercriminals Deploy CORNFLAKE.V3 Backdoor via ClickFix Tactic and Fake CAPTCHA Pages
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
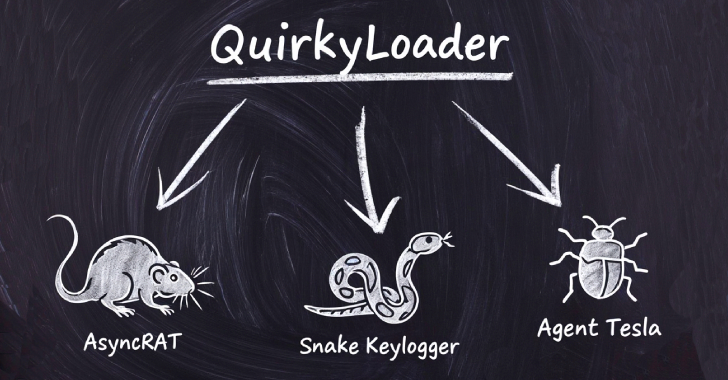
Hackers Using New QuirkyLoader Malware to Spread Agent Tesla, AsyncRAT and Snake Keylogger
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Scattered Spider Hacker Gets 10 Years, $13M Restitution for SIM Swapping Crypto Theft
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Apple Patches CVE-2025-43300 Zero-Day in iOS, iPadOS, and macOS Exploited in Targeted Attacks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
DOM-Based Extension Clickjacking Exposes Popular Password Managers to Credential and Data Theft
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
FBI Warns FSB-Linked Hackers Exploiting Unpatched Cisco Devices for Cyber Espionage
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Experts Find AI Browsers Can Be Tricked by PromptFix Exploit to Run Malicious Hidden Prompts
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
From Impact to Action: Turning BIA Insights Into Resilient Recovery
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
North Korea Uses GitHub in Diplomat Cyber Attacks as IT Worker Scheme Hits 320+ Firms
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Apache ActiveMQ Flaw Exploited to Deploy DripDropper Malware on Cloud Linux Systems
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Public Exploit for Chained SAP Flaws Exposes Unpatched Systems to Remote Code Execution
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
U.K. Government Drops Apple Encryption Backdoor Order After U.S. Civil Liberties Pushback
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Why Your Security Culture is Critical to Mitigating Cyber Risk
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
PyPI Blocks 1,800 Expired-Domain Emails to Prevent Account Takeovers and Supply Chain Attacks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
⚡ Weekly Recap: NFC Fraud, Curly COMrades, N-able Exploits, Docker Backdoors & More
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Malicious PyPI and npm Packages Discovered Exploiting Dependencies in Supply Chain Attacks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Wazuh for Regulatory Compliance
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Russian Group EncryptHub Exploits MSC EvilTwin Vulnerability to Deploy Fickle Stealer Malware
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Taiwan Web Servers Breached by UAT-7237 Using Customized Open-Source Hacking Tools
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
U.S. Sanctions Garantex and Grinex Over $100M in Ransomware-Linked Illicit Crypto Transactions
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Zero Trust + AI: Privacy in the Age of Agentic AI
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Cisco Warns of CVSS 10.0 FMC RADIUS Flaw Allowing Remote Code Execution
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
New HTTP/2 'MadeYouReset' Vulnerability Enables Large-Scale DoS Attacks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Hackers Found Using CrossC2 to Expand Cobalt Strike Beacon’s Reach to Linux and macOS
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Have You Turned Off Your Virtual Oven?
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
New Android Malware Wave Hits Banking via NFC Relay Fraud, Call Hijacking, and Root Exploits
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Simple Steps for Attack Surface Reduction
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Google Requires Crypto App Licenses in 15 Regions as FBI Warns of $9.9M Scam Losses
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
New PS1Bot Malware Campaign Uses Malvertising to Deploy Multi-Stage In-Memory Attacks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Zoom and Xerox Release Critical Security Updates Fixing Privilege Escalation and RCE Flaws
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Fortinet Warns About FortiSIEM Vulnerability (CVE-2025-25256) With In-the-Wild Exploit Code
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
AI SOC 101: Key Capabilities Security Leaders Need to Know
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Webinar: What the Next Wave of AI Cyberattacks Will Look Like — And How to Survive
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Microsoft August 2025 Patch Tuesday Fixes Kerberos Zero-Day Among 111 Total New Flaws
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Researchers Spot XZ Utils Backdoor in Dozens of Docker Hub Images, Fueling Supply Chain Risks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Fortinet SSL VPNs Hit by Global Brute-Force Wave Before Attackers Shift to FortiManager
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Cybercrime Groups ShinyHunters, Scattered Spider Join Forces in Extortion Attacks on Businesses
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
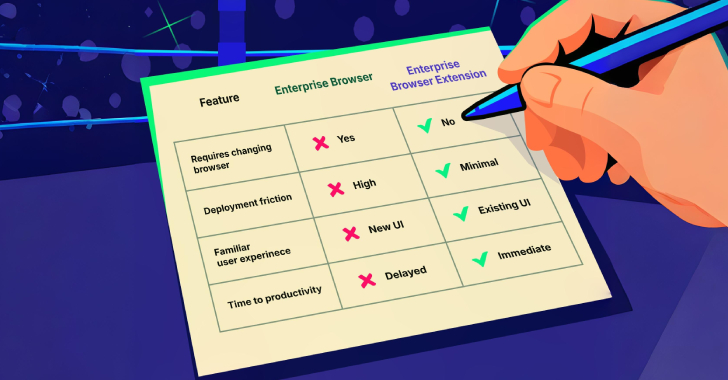
The Ultimate Battle: Enterprise Browsers vs. Secure Browser Extensions
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Dutch NCSC Confirms Active Exploitation of Citrix NetScaler CVE-2025-6543 in Critical Sectors
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
New TETRA Radio Encryption Flaws Expose Law Enforcement Communications
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
⚡ Weekly Recap: BadCam Attack, WinRAR 0-Day, EDR Killer, NVIDIA Flaws, Ransomware Attacks & More
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
6 Lessons Learned: Focusing Security Where Business Value Lives
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
New Win-DDoS Flaws Let Attackers Turn Public Domain Controllers into DDoS Botnet via RPC, LDAP
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
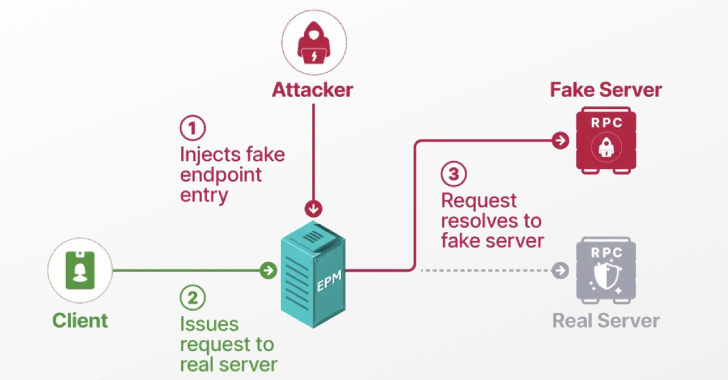
Researchers Detail Windows EPM Poisoning Exploit Chain Leading to Domain Privilege Escalation
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Researchers Reveal ReVault Attack Targeting Dell ControlVault3 Firmware in 100+ Laptop Models
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Researchers Uncover GPT-5 Jailbreak and Zero-Click AI Agent Attacks Exposing Cloud and IoT Systems
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
AI Tools Fuel Brazilian Phishing Scam While Efimer Trojan Steals Crypto from 5,000 Victims
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Leaked Credentials Up 160%: What Attackers Are Doing With Them
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
RubyGems, PyPI Hit by Malicious Packages Stealing Credentials, Crypto, Forcing Security Changes
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
SocGholish Malware Spread via Ad Tools; Delivers Access to LockBit, Evil Corp, and Others
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Malicious Go, npm Packages Deliver Cross-Platform Malware, Trigger Remote Data Wipes
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Microsoft Discloses Exchange Server Flaw Enabling Silent Cloud Access in Hybrid Setups
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Researchers Uncover ECScape Flaw in Amazon ECS Enabling Cross-Task Credential Theft
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Fake VPN and Spam Blocker Apps Tied to VexTrio Used in Ad Fraud, Subscription Scams
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Trend Micro Confirms Active Exploitation of Critical Apex One Flaws in On-Premise Systems
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
CISA Adds 3 D-Link Vulnerabilities to KEV Catalog Amid Active Exploitation Evidence
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Cursor AI Code Editor Vulnerability Enables RCE via Malicious MCP File Swaps Post Approval
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Misconfigurations Are Not Vulnerabilities: The Costly Confusion Behind Security Risks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
15,000 Fake TikTok Shop Domains Deliver Malware, Steal Crypto via AI-Driven Scam Campaign
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
SonicWall Investigating Potential SSL VPN Zero-Day After 20+ Targeted Attacks Reported
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
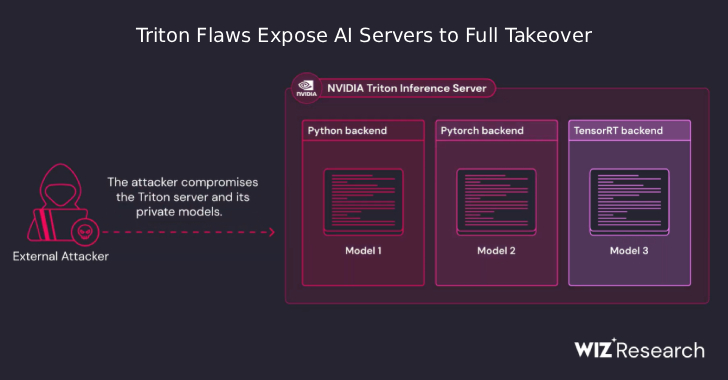
NVIDIA Triton Bugs Let Unauthenticated Attackers Execute Code and Hijack AI Servers
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Vietnamese Hackers Use PXA Stealer, Hit 4,000 IPs and Steal 200,000 Passwords Globally
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
⚡ Weekly Recap: VPN 0-Day, Encryption Backdoor, AI Malware, macOS Flaw, ATM Hack & More
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Man-in-the-Middle Attack Prevention Guide
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
The Wild West of Shadow IT
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
PlayPraetor Android Trojan Infects 11,000+ Devices via Fake Google Play Pages and Meta Ads
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
CL-STA-0969 Installs Covert Malware in Telecom Networks During 10-Month Espionage Campaign
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
New ‘Plague’ PAM Backdoor Exposes Critical Linux Systems to Silent Credential Theft
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Akira Ransomware Exploits SonicWall VPNs in Likely Zero-Day Attack on Fully-Patched Devices
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Cursor AI Code Editor Fixed Flaw Allowing Attackers to Run Commands via Prompt Injection
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
You Are What You Eat: Why Your AI Security Tools Are Only as Strong as the Data You Feed Them
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Storm-2603 Deploys DNS-Controlled Backdoor in Warlock and LockBit Ransomware Attacks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Experts Detect Multi-Layer Redirect Tactic Used to Steal Microsoft 365 Login Credentials
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
N. Korean Hackers Used Job Lures, Cloud Account Access, and Malware to Steal Millions in Crypto
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
AI-Driven Trends in Endpoint Security: What the 2025 Gartner® Magic Quadrant™ Reveals
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Alert Fatigue, Data Overload, and the Fall of Traditional SIEMs
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Hackers Exploit Critical WordPress Theme Flaw to Hijack Sites via Remote Plugin Install
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Hackers Use Facebook Ads to Spread JSCEAL Malware via Fake Cryptocurrency Trading Apps
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
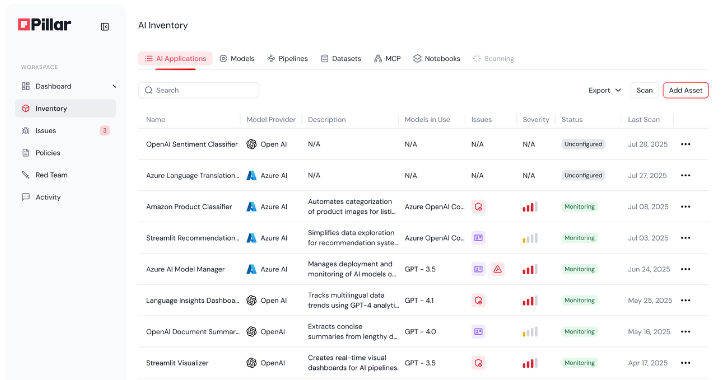
Product Walkthrough: A Look Inside Pillar's AI Security Platform
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Google Launches DBSC Open Beta in Chrome and Enhances Patch Transparency via Project Zero
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Hackers Exploit SAP Vulnerability to Breach Linux Systems and Deploy Auto-Color Malware
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Scattered Spider Hacker Arrests Halt Attacks, But Copycat Threats Sustain Security Pressure
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
PyPI Warns of Ongoing Phishing Campaign Using Fake Verification Emails and Lookalike Domain
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
How the Browser Became the Main Cyber Battleground
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Cybercriminals Use Fake Apps to Steal Data and Blackmail Users Across Asia’s Mobile Networks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Why React Didn't Kill XSS: The New JavaScript Injection Playbook
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Hackers Breach Toptal GitHub, Publish 10 Malicious npm Packages With 5,000 Downloads
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
⚡ Weekly Recap — SharePoint Breach, Spyware, IoT Hijacks, DPRK Fraud, Crypto Drains and More
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Scattered Spider Hijacks VMware ESXi to Deploy Ransomware on Critical U.S. Infrastructure
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Critical Flaws in Niagara Framework Threaten Smart Buildings and Industrial Systems Worldwide
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
U.S. Sanctions Firm Behind N. Korean IT Scheme; Arizona Woman Jailed for Running Laptop Farm
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Patchwork Targets Turkish Defense Firms with Spear-Phishing Using Malicious LNK Files
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Soco404 and Koske Malware Target Cloud Services with Cross-Platform Cryptomining Attacks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Overcoming Risks from Chinese GenAI Tool Usage
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Critical Mitel Flaw Lets Hackers Bypass Login, Gain Full Access to MiVoice MX-ONE Systems
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
CastleLoader Malware Infects 469 Devices Using Fake GitHub Repos and ClickFix Phishing
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Sophos and SonicWall Patch Critical RCE Flaws Affecting Firewalls and SMA 100 Devices
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Watch This Webinar to Uncover Hidden Flaws in Login, AI, and Digital Trust — and Fix Them
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Pentests once a year? Nope. It’s time to build an offensive SOC
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Storm-2603 Exploits SharePoint Flaws to Deploy Warlock Ransomware on Unpatched Systems
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Europol Arrests XSS Forum Admin in Kyiv After 12-Year Run Operating Cybercrime Marketplace
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
New Coyote Malware Variant Exploits Windows UI Automation to Steal Banking Credentials
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Google Launches OSS Rebuild to Expose Malicious Code in Widely Used Open-Source Packages
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
CISA Orders Urgent Patching After Chinese Hackers Exploit SharePoint Flaws in Live Attacks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Cisco Confirms Active Exploits Targeting ISE Flaws Enabling Unauthenticated Root Access
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Credential Theft and Remote Access Surge as AllaKore, PureRAT, and Hijack Loader Proliferate
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
How to Advance from SOC Manager to CISO?
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Hackers Exploit SharePoint Zero-Day Since July 7 to Steal Keys, Maintain Persistent Access
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
China-Linked Hackers Launch Targeted Espionage Campaign on African IT Infrastructure
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
⚡ Weekly Recap: SharePoint 0-Day, Chrome Exploit, macOS Spyware, NVIDIA Toolkit RCE and More
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Assessing the Role of AI in Zero Trust
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
PoisonSeed Hackers Bypass FIDO Keys Using QR Phishing and Cross-Device Sign-In Abuse
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Microsoft Releases Urgent Patch for SharePoint RCE Flaw Exploited in Ongoing Cyber Attacks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
3,500 Websites Hijacked to Secretly Mine Crypto Using Stealth JavaScript and WebSocket Tactics
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
EncryptHub Targets Web3 Developers Using Fake AI Platforms to Deploy Fickle Stealer Malware
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Critical Unpatched SharePoint Zero-Day Actively Exploited, Breaches 75+ Company Servers
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Malware Injected into 7 npm Packages After Maintainer Tokens Stolen in Phishing Attack
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Malware Injected into 5 npm Packages After Maintainer Tokens Stolen in Phishing Attack
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
China's Massistant Tool Secretly Extracts SMS, GPS Data, and Images From Confiscated Phones
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
UNG0002 Group Hits China, Hong Kong, Pakistan Using LNK Files and RATs in Twin Campaigns
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Ivanti Zero-Days Exploited to Drop MDifyLoader and Launch In-Memory Cobalt Strike Attacks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Critical NVIDIA Container Toolkit Flaw Allows Privilege Escalation on AI Cloud Services
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Google Sues 25 Chinese Entities Over BADBOX 2.0 Botnet Affecting 10M Android Devices
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
From Backup to Cyber Resilience: Why IT Leaders Must Rethink Backup in the Age of Ransomware
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Hackers Use GitHub Repositories to Host Amadey Malware and Data Stealers, Bypassing Filters
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Europol Disrupts NoName057(16) Hacktivist Group Linked to DDoS Attacks Against Ukraine
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Chinese Hackers Target Taiwan's Semiconductor Sector with Cobalt Strike, Custom Backdoors
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Cisco Warns of Critical ISE Flaw Allowing Unauthenticated Attackers to Execute Root Code
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Hackers Leverage Microsoft Teams to Spread Matanbuchus 3.0 Malware to Targeted Firms
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
UNC6148 Backdoors Fully-Patched SonicWall SMA 100 Series Devices with OVERSTEP Rootkit
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Critical Golden dMSA Attack in Windows Server 2025 Enables Cross-Domain Attacks and Persistent Access
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Deepfakes. Fake Recruiters. Cloned CFOs — Learn How to Stop AI-Driven Attacks in Real Time
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Urgent: Google Releases Critical Chrome Update for CVE-2025-6558 Exploit Active in the Wild
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Google AI "Big Sleep" Stops Exploitation of Critical SQLite Vulnerability Before Hackers Act
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
State-Backed HazyBeacon Malware Uses AWS Lambda to Steal Data from SE Asian Governments
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
AsyncRAT's Open-Source Code Sparks Surge in Dangerous Malware Variants Across the Globe
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
North Korean Hackers Flood npm Registry with XORIndex Malware in Ongoing Attack Campaign
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
The Unusual Suspect: Git Repos
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
New PHP-Based Interlock RAT Variant Uses FileFix Delivery Mechanism to Target Multiple Industries
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
⚡ Weekly Recap: Scattered Spider Arrests, Car Exploits, macOS Malware, Fortinet RCE and More
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
CBI Shuts Down £390K U.K. Tech Support Scam, Arrests Key Operatives in Noida Call Center
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
eSIM Vulnerability in Kigen's eUICC Cards Exposes Billions of IoT Devices to Malicious Attacks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Over 600 Laravel Apps Exposed to Remote Code Execution Due to Leaked APP_KEYs on GitHub
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Fortinet Releases Patch for Critical SQL Injection Flaw in FortiWeb (CVE-2025-25257)
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
PerfektBlue Bluetooth Vulnerabilities Expose Millions of Vehicles to Remote Code Execution
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Securing Data in the AI Era
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Critical Wing FTP Server Vulnerability (CVE-2025-47812) Actively Being Exploited in the Wild
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Iranian-Backed Pay2Key Ransomware Resurfaces with 80% Profit Share for Cybercriminals
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
CISA Adds Citrix NetScaler CVE-2025-5777 to KEV Catalog as Active Exploits Target Enterprises
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Critical mcp-remote Vulnerability Enables Remote Code Execution, Impacting 437,000+ Downloads
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Fake Gaming and AI Firms Push Malware on Cryptocurrency Users via Telegram and Discord
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
What Security Leaders Need to Know About AI Governance for SaaS
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Gold Melody IAB Exploits Exposed ASP.NET Machine Keys for Unauthorized Access to Targets
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
DoNot APT Expands Operations, Targets European Foreign Ministries with LoptikMod Malware
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Chinese Hacker Xu Zewei Arrested for Ties to Silk Typhoon Group and U.S. Cyber Attacks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Microsoft Patches 130 Vulnerabilities, Including Critical Flaws in SPNEGO and SQL Server
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Hackers Use Leaked Shellter Tool License to Spread Lumma Stealer and SectopRAT Malware
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Malicious Pull Request Targets 6,000+ Developers via Vulnerable Ethcode VS Code Extension
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
5 Ways Identity-based Attacks Are Breaching Retail
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
RondoDox Botnet Exploits Flaws in TBK DVRs and Four-Faith Routers to Launch DDoS Attacks
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
⚡ Weekly Recap: Chrome 0-Day, Ivanti Exploits, MacOS Stealers, Crypto Heists and More
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Manufacturing Security: Why Default Passwords Must Go
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Taiwan NSB Alerts Public on Data Risks from Douyin, Weibo, and RedNote Over China Ties
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
Taiwan NSB Alerts Public on Data Risks from TikTok, Weibo, and RedNote Over China Ties
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …
NightEagle APT Exploits Microsoft Exchange Flaw to Target China's Military and Tech Sectors
This content is restricted to site members. If you are an existing user, please log in. New users may register below.Existing Users …